Do you know the story about the motorcycle? Well, there are two motorcycles. One that was dropped and the other, that will be dropped. The same can be said about hacking.
So if you’re like me – you’re probably reading this on your phone, in your car, at a red light (I hope) or parked. Or, if you’re like some of my clients, you are reading this on your iPad mini, on your yacht on Nantucket, or maybe even in the Seychelles. It is August after all.
Often, I ask my clients to review an important documents – or they send me one for my review – and we email a documents and files back and forth and from one person to many while we determine how best to proceed. So picture yourself, whether it is an investment decision or a litigation or a transaction.
You know the drill right? You can picture yourself, whether it is an investment decision or a litigation or a transaction, sending document drafts back and forth.
What about documents that you draft on your work computer (which you also use personally) and email it to yourself to work on over the weekend or from home? Ever do that? Or, maybe you upload documents to a cloud server like Google Drive or Dropbox?
- Info Sent Over The Internet (via Email) Goes Thru Many Hands
For example, this list is all the places the document takes between my computer and a hypothetical recipient located at the Nantucket Boat Basin (There is no private info here; it is simply a trace route from my server to a public web domain address for illustration only). This trace route shows all stops that data takes between me and the end point.
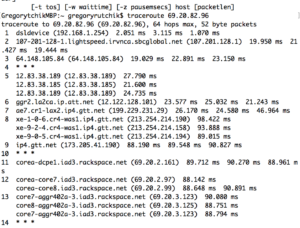
2) Identifying the Risks:
The risk is simple:
- Your personal or corporate info could be put up on the web,
- held for ransom (See below)
- given to the other side in your current transaction or litigation
- tax returns filed and refunds taken (this happens more often than I can imagine);
- or worse (Remember the Lifelock guy? ID stolen thirteen 13) times!!)
- Security CEO had his id taken and someone filed his bankruptcy! (He got it reversed but still)
At the source of the problem is very bad people wanting to take money and make your and your client’s lives a nightmare. More specifically, the bad people may unwittingly stumble on confidential info that will disrupt your business or personal objectives. And, they are simply getting more brazen, because the tools they use are even easier for them to get.
In May 2017, the Wannacry hack (or more accurately technology developed by the US National Security Agency), affected many who lost access to critical data unless they paid a ransom. It will happen again and it will only get worse because tools to gain access to the Internet and all connected devices readily exist.
– Many did not call law enforcement;
– Most did not have sufficient back ups;
– Even if they did have back ups, the data’s confidentiality was compromised (probably); and
– Many of those affected were family offices.
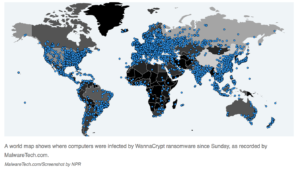
This map posted by NPR reflects the broad swath of the effected:
Ernest and Young Identifies the Problems in the following grid:
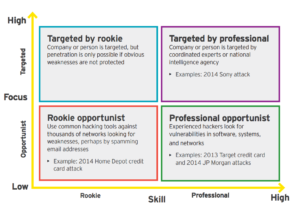
(Source E&Y: https://webforms.ey.com/Publication/vwLUAssets/ey-pdf-cybersecurity-protecting-a-family-office/$FILE/ey-cybersecurity-protecting-a-family-office.pdf)
2) To Know ‘Thyself’ Is To Know Your Risk:
a) Map Every Connection of Your Network and Have an IT Professional Ethically Hack Your Network
Here is an example of a map:
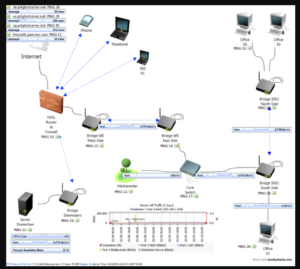
Source: https://www.paessler.com/network-mapping
You might even try it for free for your own network: https://www.paessler.com/download/prtg-download (This is not an endorsement but rather a recommendation that you had better start getting familiar with all of the doors and windows into your network. Call me if you want the recommendation of recommended professionals)
Think about all the devices, computers, wi-fi modems (even the ones on boats), Apple watches, iPhones, ipads, cloud storage, lap tops etc that your users use!
b) A Note About Passwords:
The truth is that the biggest risk is that your passwords will be accessed (not even hacked) by a former employee, a contractor who gets curious, or even an existing employee. How would you know if someone other than an authorized individual accessed YOUR machine while you were away, your account, your cloud storage? You wouldn’t.



